Buffer Overflow
Buffer overflow itself is a process that goes on inside a computer memory system in which there is an normal process at the time of the temporary data storage in memory i.e. when there is data that will be stored exceeds the capacity of the buffer (temporary storage) in memory.
FUZZER
fuzzer itself is a word that is widely used in the world of science technology one is fuzzy logic, but this discussion on fuzzer no his relationship with fuzzy logic, Fuzzer is a mention to the applications used on the process of fuzzing.
FUZZING
fuzzing is an early stage which is sure to be done by a security researcher, an application will be in line to manage the data that is not normal, so it will be seen how applications handle data as well as the process of error handling by the application, from the process here, a researcher can see if there's a gap in security application that can be exploited.
Toolstools that will be used as follows :
* Ollydbg as a debugger
* Fuzzer to do the process Fuzzing
* Phyton, used to create an application fuzzer and exploit
Before we start you need to have the application of EASY RM TO MP3 CONVERTER, like the following :
Buffer overflow itself is a process that goes on inside a computer memory system in which there is an normal process at the time of the temporary data storage in memory i.e. when there is data that will be stored exceeds the capacity of the buffer (temporary storage) in memory.
FUZZER
fuzzer itself is a word that is widely used in the world of science technology one is fuzzy logic, but this discussion on fuzzer no his relationship with fuzzy logic, Fuzzer is a mention to the applications used on the process of fuzzing.
FUZZING
fuzzing is an early stage which is sure to be done by a security researcher, an application will be in line to manage the data that is not normal, so it will be seen how applications handle data as well as the process of error handling by the application, from the process here, a researcher can see if there's a gap in security application that can be exploited.
Toolstools that will be used as follows :
* Ollydbg as a debugger
* Fuzzer to do the process Fuzzing
* Phyton, used to create an application fuzzer and exploit
Before we start you need to have the application of EASY RM TO MP3 CONVERTER, like the following :
For the application EASY RM TO MP3 CONVERTER, so here I am trying to make a simple fuzzer can send data at Mp3 protocol. the fuzzer is created using a language Python.
as the example below :
as the example below :
Now we run does occur on the application crash Easy RM MP3 converter,
in the event of a crash it will arise as follows :
now start to use Ollydbg,so we know the crash it on the EIP does not,
Open Ollydbg and Easy RM MP3 converter, the Ollydbg click file-> tattach->select RM2MP3Converter->attach->and then Turn on and then run RM2MP3, click load->the input file name and files of type->Open to clarify do as follows :
Open Ollydbg and Easy RM MP3 converter, the Ollydbg click file-> tattach->select RM2MP3Converter->attach->and then Turn on and then run RM2MP3, click load->the input file name and files of type->Open to clarify do as follows :
 |
|
|
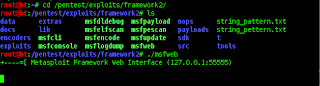
ow start to figure out how many bytes, then using pattern_create, run the command as follows:
./pattern_create.rb > 27000 string_pattern .txt
already seen the string pattern as much as 27000 character, continue with place the string on a fuzzer,, run as before.. Now use the pettern_offset application will calculate how many bytes of data from the initial pattern to stirng contained in such registersdo konsole as below : rebuilds created to change the value of the EIP be DEADBEEF, as follows: If it looks like the above, proceed to determine which libraries you want to use, double click on the file name, then it will appear as follows.
It appears as below, now do right click in the maiwindow: Search For-> Command.
the input JMP ESP in window and press the find Command Find continue by created a mouse button as follows :
run it back like before so that the results are as follows:
then right click Select BreakPoint->Memory, on access
now run by making a payload, do as follows :
Open a web browser, go to the address http://127.0.0.1:5555.
the configuration menu of the payload type of the shell, as shown in the following :
| |||||||||||||||||||||||||||||||





















No comments:
Post a Comment